Security & Trust on SaladCloud
Everyday, 100s of businesses and 1000s of individuals trust SaladCloud with their data, applications & resources. Your trust is critical to us.
Our "All Truth, No Bullshit" brand pillar means you can expect full honesty and transparency from us.
We are committed to ensuring SaladCloud plays a vital role in your security posture, and we strive to provide you with a secure-by-default experience. Read on to learn more about the security of Salad's products, platform, and infrastructure, our policies and procedures, and best practices to keep you and your customers secure.

Trusted by developers from:
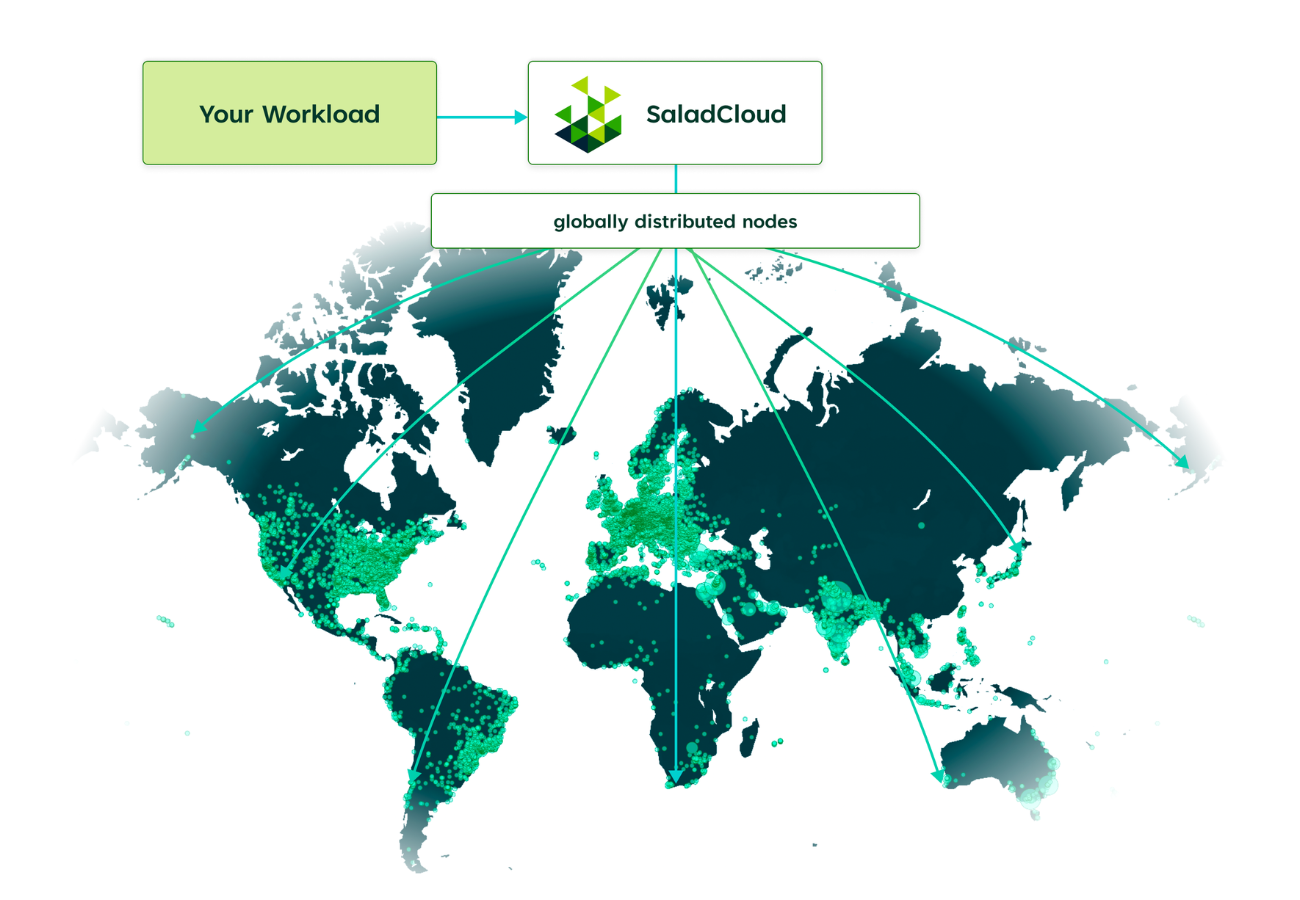
SaladCloud Architecture
Every day, 1000s of users share their resources on SaladCloud for rewards while 100s of businesses run workloads in a secure, affordable & sustainable manner.
Salad's Security Pillars
Trust and security is everything on the cloud. We have several layers of security to help keep your containers safe.
Product Security
Every product on Salad's distributed network has its own set of unique features & capabilities to provide a secure-by-default experience.
Platform Security
From authentication to logging and everything in between, the SaladCloud platform has multiple layers to ensure the security and privacy of your workloads.
Infrastructure Security
All third-party vendors and service providers are held to the highest level of security & compliance requirements in accordance with industry standards.
Trust Rating System
Every node on the SaladCloud network earns a trust rating based on their behavior & performance. Only nodes that maintain a solid trust rating are eligible for workloads.
Shared Responsiblity
All contributors to our network - Salad, resource providers, and users - share responsibility to ensure the overall security and quality of the network.
Data Security
All data and environment variables are encrypted in transit and at rest via TLS and modern cipher suites.

Compliance And The Community Cloud
Salad Technologies is SOC 2 Type I Compliant, reinforcing our commitment to democratize the cloud while ensuring the highest standards of security & compliance.
Secure Products.
- Container images and configuration settings are encrypted at-rest and in-transit.
- External container registry credentials are used to pull a container image to our cache and then immediately discarded.
- Inbound network connections to containers are blocked by default.
- Container logs may be streamed to an external logging service for auditing.
- Container images are encrypted at-rest and in-transit.
- Clients are required to use strong TLS encryption algorithms.
- Sessions are authenticated with short-lived tokens and fine-grained access.
- Requests and responses are encrypted at-rest and in-transit.
- Webhook callbacks are required to use TLS and provide strong digital signatures.
- Completed jobs are deleted after 24 hours.
- Containers are isolated from each other and exposed through the gateway on a specific port using a WireGuard VPN.
- Clients are required to use strong TLS encryption algorithms.
- Routes are protected via dedicated DDoS hardware.
Frequently Asked Questions
Common Security Questions from SaladCloud Users
Salad nodes are crowd-sourced, high-end gaming computers. This inherently presents some security and privacy concerns depending on your use case.
For example, traffic between your workload and the Internet may be logged by intermediate networking equipment. If the connection uses strong encryption, the content is not visible and protected. However, even if the connection uses strong encryption, the destination IP address is still available in plain text. Performing a reverse DNS query on the IP address may disclose information about the type of workload running on the SaladCloud Node.
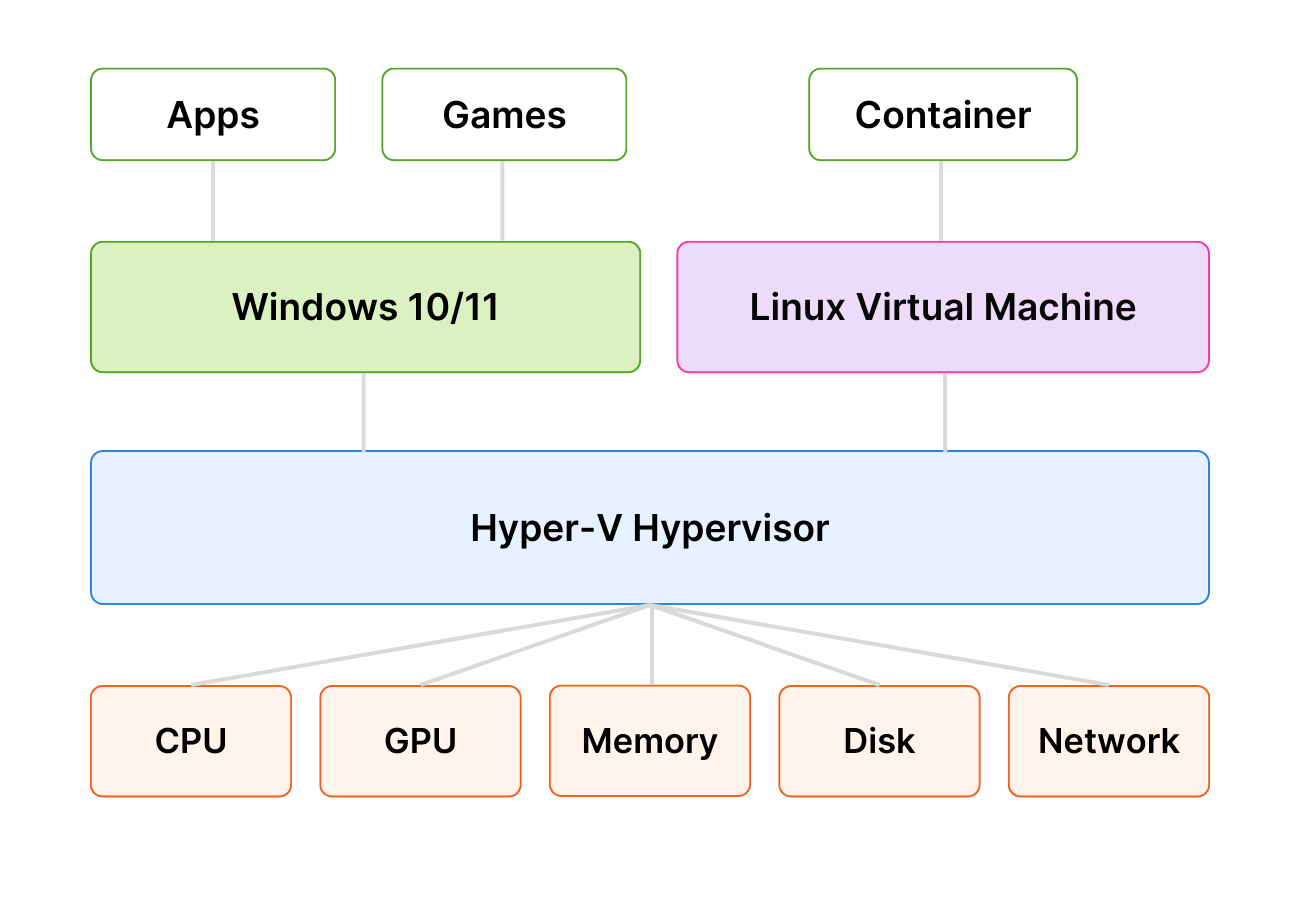
Additionally, while we rely on Hyper-V hypervisor and Linux container technology isolation, Salad takes many measures to detect and minimize the threat of these risks, and there are many technical approaches you can take to further minimize the risks. We strongly recommend you get in touch with our team before launching a new workload to review any security or privacy concerns.
Due to the unique nature of SaladCloud’s infrastructure, not all workloads are a fit for our network. Applications with highly specific regulatory and compliance requirements and high data-to-compute ratio are often not a good fit for SaladCloud. We encourage you to get in touch with our team so that we can review your specific needs to identify whether or not your requirements are compatible with the network.
Applications with highly specific regulatory/compliance needs and high data-to-compute ratio are often not a good fit for SaladCloud. Please get in touch with us to discuss your specific use case.




